corel
February 8, 2025, 3:18pm
1
wie gesagt versuche es mal wieder, mitoxideshop.log for more details.
[08 Feb 16:12:07.191051 2025] [uncaught error] [type E_ERROR] [file /myhomepfad/oxid/vendor/oxid-esales/oxideshop-ce/source/Core/Database/Adapter/Doctrine/Database.php] [line 955] [code ] [message Uncaught PDOException: SQLSTATE[42000]: Syntax error or access violation: 1305 FUNCTION usr_ud27_14_4.DECODE does not exist in /myhomepfad/oxid/vendor/doctrine/dbal/lib/Doctrine/DBAL/Driver/PDOStatement.php:117
Stack trace:
#0 /myhomepfad/oxid/vendor/doctrine/dbal/lib/Doctrine/DBAL/Driver/PDOStatement.php(117): PDOStatement->execute()
#1 /myhomepfad/oxid/vendor/doctrine/dbal/lib/Doctrine/DBAL/Connection.php(1304): Doctrine\DBAL\Driver\PDOStatement->execute()
#2 /myhomepfad/oxid/vendor/doctrine/dbal/lib/Doctrine/DBAL/Connection.php(665): Doctrine\DBAL\Connection->executeQuery()
#3 /myhomepfad/oxid/vendor/oxid-esales/oxideshop-ce/source/Core/Database/Adapter/Doctrine/Database.php(312): Doctrine\DBAL\Connection->fetchColumn()
#4 /myhomepfad/oxid/vendor/oxid-esales/oxideshop-ce/source/Core/Module/ModuleVariablesLocator.php(129): OxidEsales\EshopCommunity\Core\Database\Adapter\Doctrine\Database->getOne()
#5 /myhomepfad/oxid/vendor/oxid-esales/oxideshop-ce/source/Core/Module/ModuleVariablesLocator.php(60): OxidEsales\EshopCommunity\Core\Module\ModuleVariablesLocator->getModuleVarFromDB()
#6 /myhomepfad/oxid/vendor/oxid-esales/oxideshop-ce/source/Core/Module/ModuleChainsGenerator.php(477): OxidEsales\EshopCommunity\Core\Module\ModuleVariablesLocator->getModuleVariable()
#7 /myhomepfad/oxid/vendor/oxid-esales/oxideshop-ce/source/Core/Module/ModuleChainsGenerator.php(92): OxidEsales\EshopCommunity\Core\Module\ModuleChainsGenerator->getClassExtensionChain()
#8 /myhomepfad/oxid/vendor/oxid-esales/oxideshop-ce/source/Core/Module/ModuleChainsGenerator.php(74): OxidEsales\EshopCommunity\Core\Module\ModuleChainsGenerator->getFullChain()
#9 /myhomepfad/oxid/vendor/oxid-esales/oxideshop-ce/source/Core/Module/ModuleChainsGenerator.php(53): OxidEsales\EshopCommunity\Core\Module\ModuleChainsGenerator->getActiveChain()
#10 /myhomepfad/oxid/vendor/oxid-esales/oxideshop-ce/source/Core/UtilsObject.php(269): OxidEsales\EshopCommunity\Core\Module\ModuleChainsGenerator->createClassChain()
#11 /myhomepfad/oxid/vendor/oxid-esales/oxideshop-ce/source/Core/UtilsObject.php(219): OxidEsales\EshopCommunity\Core\UtilsObject->getClassName()
#12 /myhomepfad/oxid/source/oxfunctions.php(104): OxidEsales\EshopCommunity\Core\UtilsObject->oxNew()
#13 /myhomepfad/oxid/vendor/oxid-esales/oxideshop-db-views-generator/src/ViewsGenerator.php(37): oxNew()
#14 /myhomepfad/oxid/vendor/oxid-esales/oxideshop-db-views-generator/generate_views.php(80): OxidEsales\DatabaseViewsGenerator\ViewsGenerator->generate()
#15 /myhomepfad/oxid/vendor/oxid-esales/oxideshop-db-views-generator/oe-eshop-db_views_generate(4): require_once('...')
#16 /myhomepfad/oxid/vendor/bin/oe-eshop-db_views_generate(117): include('...')
#17 {main}
Next Doctrine\DBAL\Driver\PDO\Exception: SQLSTATE[42000]: Syntax error or access violation: 1305 FUNCTION usr_ud27_14_4.DECODE does not exist in /myhomepfad/oxid/vendor/doctrine/dbal/lib/Doctrine/DBAL/Driver/PDO/Exception.php:18
Stack trace:
#0 /myhomepfad/oxid/vendor/doctrine/dbal/lib/Doctrine/DBAL/Driver/PDOStatement.php(119): Doctrine\DBAL\Driver\PDO\Exception::new()
#1 /myhomepfad/oxid/vendor/doctrine/dbal/lib/Doctrine/DBAL/Connection.php(1304): Doctrine\DBAL\Driver\PDOStatement->execute()
#2 /myhomepfad/oxid/vendor/doctrine/dbal/lib/Doctrine/DBAL/Connection.php(665): Doctrine\DBAL\Connection->executeQuery()
#3 /myhomepfad/oxid/vendor/oxid-esales/oxideshop-ce/source/Core/Database/Adapter/Doctrine/Database.php(312): Doctrine\DBAL\Connection->fetchColumn()
#4 /myhomepfad/oxid/vendor/oxid-esales/oxideshop-ce/source/Core/Module/ModuleVariablesLocator.php(129): OxidEsales\EshopCommunity\Core\Database\Adapter\Doctrine\Database->getOne()
#5 /myhomepfad/oxid/vendor/oxid-esales/oxideshop-ce/source/Core/Module/ModuleVariablesLocator.php(60): OxidEsales\EshopCommunity\Core\Module\ModuleVariablesLocator->getModuleVarFromDB()
#6 /myhomepfad/oxid/vendor/oxid-esales/oxideshop-ce/source/Core/Module/ModuleChainsGenerator.php(477): OxidEsales\EshopCommunity\Core\Module\ModuleVariablesLocator->getModuleVariable()
#7 /myhomepfad/oxid/vendor/oxid-esales/oxideshop-ce/source/Core/Module/ModuleChainsGenerator.php(92): OxidEsales\EshopCommunity\Core\Module\ModuleChainsGenerator->getClassExtensionChain()
#8 /myhomepfad/oxid/vendor/oxid-esales/oxideshop-ce/source/Core/Module/ModuleChainsGenerator.php(74): OxidEsales\EshopCommunity\Core\Module\ModuleChainsGenerator->getFullChain()
#9 /myhomepfad/oxid/vendor/oxid-esales/oxideshop-ce/source/Core/Module/ModuleChainsGenerator.php(53): OxidEsales\EshopCommunity\Core\Module\ModuleChainsGenerator->getActiveChain()
#10 /myhomepfad/oxid/vendor/oxid-esales/oxideshop-ce/source/Core/UtilsObject.php(269): OxidEsales\EshopCommunity\Core\Module\ModuleChainsGenerator->createClassChain()
#11 /myhomepfad/oxid/vendor/oxid-esales/oxideshop-ce/source/Core/UtilsObject.php(219): OxidEsales\EshopCommunity\Core\UtilsObject->getClassName()
#12 /myhomepfad/oxid/source/oxfunctions.php(104): OxidEsales\EshopCommunity\Core\UtilsObject->oxNew()
#13 /myhomepfad/oxid/vendor/oxid-esales/oxideshop-db-views-generator/src/ViewsGenerator.php(37): oxNew()
#14 /myhomepfad/oxid/vendor/oxid-esales/oxideshop-db-views-generator/generate_views.php(80): OxidEsales\DatabaseViewsGenerator\ViewsGenerator->generate()
#15 /myhomepfad/oxid/vendor/oxid-esales/oxideshop-db-views-generator/oe-eshop-db_views_generate(4): require_once('...')
#16 /myhomepfad/oxid/vendor/bin/oe-eshop-db_views_generate(117): include('...')
#17 {main}
Next Doctrine\DBAL\Exception\DriverException: An exception occurred while executing 'SELECT DECODE( oxvarvalue , ? ) FROM oxconfig WHERE oxvarname = ? AND oxshopid = ?' with params ["fq45QS09_fqyx09239QQ", "aModules", 1]:
SQLSTATE[42000]: Syntax error or access violation: 1305 FUNCTION usr_ud27_14_4.DECODE does not exist in /myhomepfad/oxid/vendor/doctrine/dbal/lib/Doctrine/DBAL/Driver/AbstractMySQLDriver.php:128
Stack trace:
#0 /myhomepfad/oxid/vendor/doctrine/dbal/lib/Doctrine/DBAL/DBALException.php(182): Doctrine\DBAL\Driver\AbstractMySQLDriver->convertException()
#1 /myhomepfad/oxid/vendor/doctrine/dbal/lib/Doctrine/DBAL/DBALException.php(159): Doctrine\DBAL\DBALException::wrapException()
#2 /myhomepfad/oxid/vendor/doctrine/dbal/lib/Doctrine/DBAL/Connection.php(2222): Doctrine\DBAL\DBALException::driverExceptionDuringQuery()
#3 /myhomepfad/oxid/vendor/doctrine/dbal/lib/Doctrine/DBAL/Connection.php(1312): Doctrine\DBAL\Connection->handleExceptionDuringQuery()
#4 /myhomepfad/oxid/vendor/doctrine/dbal/lib/Doctrine/DBAL/Connection.php(665): Doctrine\DBAL\Connection->executeQuery()
#5 /myhomepfad/oxid/vendor/oxid-esales/oxideshop-ce/source/Core/Database/Adapter/Doctrine/Database.php(312): Doctrine\DBAL\Connection->fetchColumn()
#6 /myhomepfad/oxid/vendor/oxid-esales/oxideshop-ce/source/Core/Module/ModuleVariablesLocator.php(129): OxidEsales\EshopCommunity\Core\Database\Adapter\Doctrine\Database->getOne()
#7 /myhomepfad/oxid/vendor/oxid-esales/oxideshop-ce/source/Core/Module/ModuleVariablesLocator.php(60): OxidEsales\EshopCommunity\Core\Module\ModuleVariablesLocator->getModuleVarFromDB()
#8 /myhomepfad/oxid/vendor/oxid-esales/oxideshop-ce/source/Core/Module/ModuleChainsGenerator.php(477): OxidEsales\EshopCommunity\Core\Module\ModuleVariablesLocator->getModuleVariable()
#9 /myhomepfad/oxid/vendor/oxid-esales/oxideshop-ce/source/Core/Module/ModuleChainsGenerator.php(92): OxidEsales\EshopCommunity\Core\Module\ModuleChainsGenerator->getClassExtensionChain()
#10 /myhomepfad/oxid/vendor/oxid-esales/oxideshop-ce/source/Core/Module/ModuleChainsGenerator.php(74): OxidEsales\EshopCommunity\Core\Module\ModuleChainsGenerator->getFullChain()
#11 /myhomepfad/oxid/vendor/oxid-esales/oxideshop-ce/source/Core/Module/ModuleChainsGenerator.php(53): OxidEsales\EshopCommunity\Core\Module\ModuleChainsGenerator->getActiveChain()
#12 /myhomepfad/oxid/vendor/oxid-esales/oxideshop-ce/source/Core/UtilsObject.php(269): OxidEsales\EshopCommunity\Core\Module\ModuleChainsGenerator->createClassChain()
#13 /myhomepfad/oxid/vendor/oxid-esales/oxideshop-ce/source/Core/UtilsObject.php(219): OxidEsales\EshopCommunity\Core\UtilsObject->getClassName()
#14 /myhomepfad/oxid/source/oxfunctions.php(104): OxidEsales\EshopCommunity\Core\UtilsObject->oxNew()
#15 /myhomepfad/oxid/vendor/oxid-esales/oxideshop-db-views-generator/src/ViewsGenerator.php(37): oxNew()
#16 /myhomepfad/oxid/vendor/oxid-esales/oxideshop-db-views-generator/generate_views.php(80): OxidEsales\DatabaseViewsGenerator\ViewsGenerator->generate()
#17 /myhomepfad/oxid/vendor/oxid-esales/oxideshop-db-views-generator/oe-eshop-db_views_generate(4): require_once('...')
#18 /myhomepfad/oxid/vendor/bin/oe-eshop-db_views_generate(117): include('...')
#19 {main}
Next OxidEsales\Eshop\Core\Exception\DatabaseErrorException: FUNCTION usr_ud27_14_4.DECODE does not exist in /myhomepfad/oxid/vendor/oxid-esales/oxideshop-ce/source/Core/Database/Adapter/Doctrine/Database.php:955
Stack trace:
#0 /myhomepfad/oxid/vendor/oxid-esales/oxideshop-ce/source/Core/Database/Adapter/Doctrine/Database.php(314): OxidEsales\EshopCommunity\Core\Database\Adapter\Doctrine\Database->convertException()
#1 /myhomepfad/oxid/vendor/oxid-esales/oxideshop-ce/source/Core/Module/ModuleVariablesLocator.php(129): OxidEsales\EshopCommunity\Core\Database\Adapter\Doctrine\Database->getOne()
#2 /myhomepfad/oxid/vendor/oxid-esales/oxideshop-ce/source/Core/Module/ModuleVariablesLocator.php(60): OxidEsales\EshopCommunity\Core\Module\ModuleVariablesLocator->getModuleVarFromDB()
#3 /myhomepfad/oxid/vendor/oxid-esales/oxideshop-ce/source/Core/Module/ModuleChainsGenerator.php(477): OxidEsales\EshopCommunity\Core\Module\ModuleVariablesLocator->getModuleVariable()
#4 /myhomepfad/oxid/vendor/oxid-esales/oxideshop-ce/source/Core/Module/ModuleChainsGenerator.php(92): OxidEsales\EshopCommunity\Core\Module\ModuleChainsGenerator->getClassExtensionChain()
#5 /myhomepfad/oxid/vendor/oxid-esales/oxideshop-ce/source/Core/Module/ModuleChainsGenerator.php(74): OxidEsales\EshopCommunity\Core\Module\ModuleChainsGenerator->getFullChain()
#6 /myhomepfad/oxid/vendor/oxid-esales/oxideshop-ce/source/Core/Module/ModuleChainsGenerator.php(53): OxidEsales\EshopCommunity\Core\Module\ModuleChainsGenerator->getActiveChain()
#7 /myhomepfad/oxid/vendor/oxid-esales/oxideshop-ce/source/Core/UtilsObject.php(269): OxidEsales\EshopCommunity\Core\Module\ModuleChainsGenerator->createClassChain()
#8 /myhomepfad/oxid/vendor/oxid-esales/oxideshop-ce/source/Core/UtilsObject.php(219): OxidEsales\EshopCommunity\Core\UtilsObject->getClassName()
#9 /myhomepfad/oxid/source/oxfunctions.php(104): OxidEsales\EshopCommunity\Core\UtilsObject->oxNew()
#10 /myhomepfad/oxid/vendor/oxid-esales/oxideshop-db-views-generator/src/ViewsGenerator.php(37): oxNew()
#11 /myhomepfad/oxid/vendor/oxid-esales/oxideshop-db-views-generator/generate_views.php(80): OxidEsales\DatabaseViewsGenerator\ViewsGenerator->generate()
#12 /myhomepfad/oxid/vendor/oxid-esales/oxideshop-db-views-generator/oe-eshop-db_views_generate(4): require_once('...')
#13 /myhomepfad/oxid/vendor/bin/oe-eshop-db_views_generate(117): include('...')
#14 {main}
thrown]
corel
February 9, 2025, 5:40pm
2
noch eine Kleinigkeit was mache ich mit ‘composer audit’
$ composer audit
Found 17 security vulnerability advisories affecting 4 packages:
+-------------------+----------------------------------------------------------------------------------+
| Package | composer/composer |
| Severity | high |
| CVE | CVE-2024-35241 |
| Title | Composer has a command injection via malicious git branch name |
| URL | https://github.com/advisories/GHSA-47f6-5gq3-vx9c |
| Affected versions | >=2.3,<2.7.7|>=2.0,<2.2.24 |
| Reported at | 2024-06-10T21:36:32+00:00 |
+-------------------+----------------------------------------------------------------------------------+
+-------------------+----------------------------------------------------------------------------------+
| Package | composer/composer |
| Severity | high |
| CVE | CVE-2024-35242 |
| Title | Composer has multiple command injections via malicious git/hg branch names |
| URL | https://github.com/advisories/GHSA-v9qv-c7wm-wgmf |
| Affected versions | >=2.3,<2.7.7|>=2.0,<2.2.24 |
| Reported at | 2024-06-10T21:36:25+00:00 |
+-------------------+----------------------------------------------------------------------------------+
+-------------------+----------------------------------------------------------------------------------+
| Package | smarty/smarty |
| Severity | high |
| CVE | CVE-2023-28447 |
| Title | Cross site scripting vulnerability in Javascript escaping |
| URL | https://github.com/smarty-php/smarty/security/advisories/GHSA-7j98-h7fp-4vwj |
| Affected versions | <3.1.48|>=4.0.0,<4.1.1 |
| Reported at | 2023-03-28T19:41:00+00:00 |
+-------------------+----------------------------------------------------------------------------------+
+-------------------+----------------------------------------------------------------------------------+
| Package | smarty/smarty |
| Severity | medium |
| CVE | CVE-2018-25047 |
| Title | smarty_function_mailto - JavaScript injection in eval function |
| URL | https://github.com/smarty-php/smarty/issues/454 |
| Affected versions | <3.1.47|>=4.0.0,<4.2.1 |
| Reported at | 2022-09-14T11:32:14+00:00 |
+-------------------+----------------------------------------------------------------------------------+
+-------------------+----------------------------------------------------------------------------------+
| Package | smarty/smarty |
| Severity | high |
| CVE | CVE-2022-29221 |
| Title | PHP Code Injection by malicious block or filename |
| URL | https://github.com/smarty-php/smarty/security/advisories/GHSA-634x-pc3q-cf4c |
| Affected versions | <3.1.45|>=4.0.0,<4.1.1 |
| Reported at | 2022-05-17T12:59:00+00:00 |
+-------------------+----------------------------------------------------------------------------------+
+-------------------+----------------------------------------------------------------------------------+
| Package | smarty/smarty |
| Severity | medium |
| CVE | CVE-2012-4437 |
| Title | Cross-site Scripting in SmartyException |
| URL | https://github.com/advisories/GHSA-9gqj-ppv2-f2hq |
| Affected versions | <3.1.12 |
| Reported at | 2022-05-17T04:02:12+00:00 |
+-------------------+----------------------------------------------------------------------------------+
+-------------------+----------------------------------------------------------------------------------+
| Package | smarty/smarty |
| Severity | high |
| CVE | CVE-2014-8350 |
| Title | Smarty arbitrary PHP code execution |
| URL | https://github.com/advisories/GHSA-2pmx-6mm6-6v72 |
| Affected versions | <3.1.21 |
| Reported at | 2022-05-17T01:13:38+00:00 |
+-------------------+----------------------------------------------------------------------------------+
+-------------------+----------------------------------------------------------------------------------+
| Package | smarty/smarty |
| Severity | medium |
| CVE | CVE-2009-5054 |
| Title | Smarty Does Not Consider Umask Values When Setting Permissions |
| URL | https://github.com/advisories/GHSA-6m9f-8vwq-97pm |
| Affected versions | <3.0.0-beta4 |
| Reported at | 2022-05-02T04:00:47+00:00 |
+-------------------+----------------------------------------------------------------------------------+
+-------------------+----------------------------------------------------------------------------------+
| Package | smarty/smarty |
| Severity | critical |
| CVE | CVE-2011-1028 |
| Title | Smarty3 Arbitrary PHP Code Execution |
| URL | https://github.com/advisories/GHSA-6frx-2r5w-c524 |
| Affected versions | <3.0.7 |
| Reported at | 2022-04-22T00:24:15+00:00 |
+-------------------+----------------------------------------------------------------------------------+
+-------------------+----------------------------------------------------------------------------------+
| Package | smarty/smarty |
| Severity | high |
| CVE | CVE-2021-21408 |
| Title | Access to restricted PHP code by dynamic static class access |
| URL | https://github.com/smarty-php/smarty/security/advisories/GHSA-4h9c-v5vg-5m6m |
| Affected versions | <3.1.43|>=4.0.0,<4.0.3 |
| Reported at | 2022-01-10T10:48:27+00:00 |
+-------------------+----------------------------------------------------------------------------------+
+-------------------+----------------------------------------------------------------------------------+
| Package | smarty/smarty |
| Severity | high |
| CVE | CVE-2021-29454 |
| Title | Sandbox Escape by math function |
| URL | https://github.com/smarty-php/smarty/security/advisories/GHSA-29gp-2c3m-3j6m |
| Affected versions | <3.1.42|>=4.0.0,<4.0.2 |
| Reported at | 2022-01-10T00:01:43+00:00 |
+-------------------+----------------------------------------------------------------------------------+
+-------------------+----------------------------------------------------------------------------------+
| Package | smarty/smarty |
| Severity | critical |
| CVE | CVE-2021-26120 |
| Title | Smarty_Internal_Runtime_TplFunction Sandbox Escape PHP Code Injection |
| URL | https://srcincite.io/blog/2021/02/18/smarty-template-engine-multiple-sandbox-esc |
| | ape-vulnerabilities.html |
| Affected versions | <=3.1.38 |
| Reported at | 2021-01-24T22:44:07+00:00 |
+-------------------+----------------------------------------------------------------------------------+
+-------------------+----------------------------------------------------------------------------------+
| Package | smarty/smarty |
| Severity | high |
| CVE | CVE-2021-26119 |
| Title | template_object Sandbox Escape PHP Code Injection |
| URL | https://srcincite.io/blog/2021/02/18/smarty-template-engine-multiple-sandbox-esc |
| | ape-vulnerabilities.html |
| Affected versions | <=3.1.38 |
| Reported at | 2021-01-24T22:13:26+00:00 |
+-------------------+----------------------------------------------------------------------------------+
+-------------------+----------------------------------------------------------------------------------+
| Package | smarty/smarty |
| Severity | medium |
| CVE | CVE-2018-16831 |
| Title | Trusted-Directory Bypass via Path Traversal |
| URL | https://github.com/smarty-php/smarty/issues/486 |
| Affected versions | <3.1.33 |
| Reported at | 2018-04-26T19:38:08+00:00 |
+-------------------+----------------------------------------------------------------------------------+
+-------------------+----------------------------------------------------------------------------------+
| Package | smarty/smarty |
| Severity | high |
| CVE | CVE-2018-13982 |
| Title | Trusted-Directory Bypass via Path Traversal |
| URL | https://github.com/sbaresearch/advisories/tree/public/2018/SBA-ADV-20180420-01_S |
| | marty_Path_Traversal |
| Affected versions | <3.1.33 |
| Reported at | 2018-04-26T19:38:08+00:00 |
+-------------------+----------------------------------------------------------------------------------+
+-------------------+----------------------------------------------------------------------------------+
| Package | symfony/http-foundation |
| Severity | low |
| CVE | CVE-2024-50345 |
| Title | CVE-2024-50345: Open redirect via browser-sanitized URLs |
| URL | https://symfony.com/cve-2024-50345 |
| Affected versions | >=2.0.0,<3.0.0|>=3.0.0,<4.0.0|>=4.0.0,<5.0.0|>=5.0.0,<5.1.0|>=5.1.0,<5.2.0|>=5.2 |
| | .0,<5.3.0|>=5.3.0,<5.4.0|>=5.4.0,<5.4.46|>=6.0.0,<6.1.0|>=6.1.0,<6.2.0|>=6.2.0,< |
| | 6.3.0|>=6.3.0,<6.4.0|>=6.4.0,<6.4.14|>=7.0.0,<7.1.0|>=7.1.0,<7.1.7 |
| Reported at | 2024-11-05T08:00:00+00:00 |
+-------------------+----------------------------------------------------------------------------------+
+-------------------+----------------------------------------------------------------------------------+
| Package | symfony/process |
| Severity | high |
| CVE | CVE-2024-51736 |
| Title | CVE-2024-51736: Command execution hijack on Windows with Process class |
| URL | https://symfony.com/cve-2024-51736 |
| Affected versions | >=2.0.0,<3.0.0|>=3.0.0,<4.0.0|>=4.0.0,<5.0.0|>=5.0.0,<5.1.0|>=5.1.0,<5.2.0|>=5.2 |
| | .0,<5.3.0|>=5.3.0,<5.4.0|>=5.4.0,<5.4.46|>=6.0.0,<6.1.0|>=6.1.0,<6.2.0|>=6.2.0,< |
| | 6.3.0|>=6.3.0,<6.4.0|>=6.4.0,<6.4.14|>=7.0.0,<7.1.0|>=7.1.0,<7.1.7 |
| Reported at | 2024-11-05T08:00:00+00:00 |
+-------------------+----------------------------------------------------------------------------------+
Found 2 abandoned packages:
+--------------------------+----------------------------------------------------------------------------------+
| Abandoned Package | Suggested Replacement |
+--------------------------+----------------------------------------------------------------------------------+
| oxid-esales/flow-theme | oxid-esales/wave-theme |
| phpunit/php-token-stream | none |
+--------------------------+----------------------------------------------------------------------------------+
DanielS
February 10, 2025, 7:18am
3
Hallo Corel,
Der Grund der Meldung ist, dass Du mySQL 8 einsetzt. Der 6.5er OXID Shop kann damit nicht umgehen, da dieser die entfernte ENCODE() / DECODE() Funktionen nutzt. Welchsel daher bitte auf mySQL 5.7 oder MariaDb. Ab OXID 7 kannst Du dann auch mySQL 8 verwenden.
DanielS
February 10, 2025, 7:34am
4
Die Audit-Funktion zeigt die bekannte Sicherheitslücken in Deiner Compilation auf. Ich befürchte, die werden sich in OXID 6.5 nicht lösen lassen. Das liegt daran, dass allein das OXID Patch schon ein Jahr alt ist und nur noch Legacy Support erhält.
Wobei auch ein aktueller OXID 7.2 nicht ganz frei von Audit Meldungen ist. Die Frage ist nur, ob sich die Schwachstellen auch ausnutzen lassen.
corel
February 10, 2025, 7:39am
5
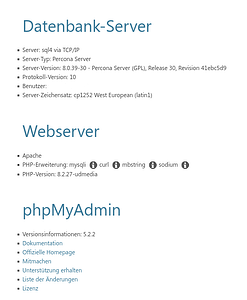
thx, ich Glaube von Seiten des ISP wird dies nicht gehen, derzeit ist diese gegeben:
Gibt es dazu alternativen ein Upgrade auf 6.14.3 oder so? Auf die 7er Version habe ich schon versucht upzudaten das funktioniert nur nicht und damit habe ich bereits Tage verbracht.
corel
February 10, 2025, 11:36am
6
nun erhalte ich jenes bei ‘oe-eshop-db_views_generate’. Wie?
./vendor/bin/oe-eshop-db_views_generate
Fatal error: Uncaught PDOException: SQLSTATE[HY000]: General error: 1347 'myDB.oxv_oxvendor_de' is not VIEW in ../vendor/doctrine/dbal/lib/Doctrine/DBAL/Driver/PDOConnection.php:55
Stack trace:
#0 ../vendor/doctrine/dbal/lib/Doctrine/DBAL/Driver/PDOConnection.php(55): PDO->exec()
#1 ../vendor/doctrine/dbal/lib/Doctrine/DBAL/Connection.php(1534): Doctrine\DBAL\Driver\PDOConnection->exec()
#2 ../vendor/doctrine/dbal/lib/Doctrine/DBAL/Connection.php(1487): Doctrine\DBAL\Connection->executeStatement()
#3 ../vendor/oxid-esales/oxideshop-ce/source/Core/Database/Adapter/Doctrine/Database.php(799): Doctrine\DBAL\Connection->executeUpdate()
#4 ../vendor/oxid-esales/oxideshop-ce/source/Core/Database/Adapter/Doctrine/Database.php(570): OxidEsales\EshopCommunity\Core\Database\Adapter\Doctrine\Database->executeUpdate()
#5 ../vendor/oxid-esales/oxideshop-ce/source/Application/Model/Shop.php(301): OxidEsales\EshopCommunity\Core\Database\Adapter\Doctrine\Database->execute()
#6 ../vendor/oxid-esales/oxideshop-ce/source/Application/Model/Shop.php(145): OxidEsales\EshopCommunity\Application\Model\Shop->cleanInvalidViews()
#7 ../vendor/oxid-esales/oxideshop-ce/source/Core/DbMetaDataHandler.php(574): OxidEsales\EshopCommunity\Application\Model\Shop->generateViews()
#8 ../vendor/oxid-esales/oxideshop-db-views-generator/src/ViewsGenerator.php(39): OxidEsales\EshopCommunity\Core\DbMetaDataHandler->updateViews()
#9 ../vendor/oxid-esales/oxideshop-db-views-generator/generate_views.php(80): OxidEsales\DatabaseViewsGenerator\ViewsGenerator->generate()
#10 ../vendor/oxid-esales/oxideshop-db-views-generator/oe-eshop-db_views_generate(4): require_once('...')
#11 ../vendor/bin/oe-eshop-db_views_generate(119): include('...')
#12 {main}
Next Doctrine\DBAL\Driver\PDO\Exception: SQLSTATE[HY000]: General error: 1347 'myDB.oxv_oxvendor_de' is not VIEW in ../vendor/doctrine/dbal/lib/Doctrine/DBAL/Driver/PDO/Exception.php:18
Stack trace:
#0 ../vendor/doctrine/dbal/lib/Doctrine/DBAL/Driver/PDOConnection.php(60): Doctrine\DBAL\Driver\PDO\Exception::new()
#1 ../vendor/doctrine/dbal/lib/Doctrine/DBAL/Connection.php(1534): Doctrine\DBAL\Driver\PDOConnection->exec()
#2 ../vendor/doctrine/dbal/lib/Doctrine/DBAL/Connection.php(1487): Doctrine\DBAL\Connection->executeStatement()
#3 ../vendor/oxid-esales/oxideshop-ce/source/Core/Database/Adapter/Doctrine/Database.php(799): Doctrine\DBAL\Connection->executeUpdate()
#4 ../vendor/oxid-esales/oxideshop-ce/source/Core/Database/Adapter/Doctrine/Database.php(570): OxidEsales\EshopCommunity\Core\Database\Adapter\Doctrine\Database->executeUpdate()
#5 ../vendor/oxid-esales/oxideshop-ce/source/Application/Model/Shop.php(301): OxidEsales\EshopCommunity\Core\Database\Adapter\Doctrine\Database->execute()
#6 ../vendor/oxid-esales/oxideshop-ce/source/Application/Model/Shop.php(145): OxidEsales\EshopCommunity\Application\Model\Shop->cleanInvalidViews()
#7 ../vendor/oxid-esales/oxideshop-ce/source/Core/DbMetaDataHandler.php(574): OxidEsales\EshopCommunity\Application\Model\Shop->generateViews()
#8 ../vendor/oxid-esales/oxideshop-db-views-generator/src/ViewsGenerator.php(39): OxidEsales\EshopCommunity\Core\DbMetaDataHandler->updateViews()
#9 ../vendor/oxid-esales/oxideshop-db-views-generator/generate_views.php(80): OxidEsales\DatabaseViewsGenerator\ViewsGenerator->generate()
#10 ../vendor/oxid-esales/oxideshop-db-views-generator/oe-eshop-db_views_generate(4): require_once('...')
#11 ../vendor/bin/oe-eshop-db_views_generate(119): include('...')
#12 {main}
Next Doctrine\DBAL\Exception\DriverException: An exception occurred while executing 'DROP VIEW IF EXISTS `oxv_oxvendor_de`':
SQLSTATE[HY000]: General error: 1347 'myDB.oxv_oxvendor_de' is not VIEW in ../vendor/doctrine/dbal/lib/Doctrine/DBAL/Driver/AbstractMySQLDriver.php:128
Stack trace:
#0 ../vendor/doctrine/dbal/lib/Doctrine/DBAL/DBALException.php(182): Doctrine\DBAL\Driver\AbstractMySQLDriver->convertException()
#1 ../vendor/doctrine/dbal/lib/Doctrine/DBAL/DBALException.php(159): Doctrine\DBAL\DBALException::wrapException()
#2 ../vendor/doctrine/dbal/lib/Doctrine/DBAL/Connection.php(2222): Doctrine\DBAL\DBALException::driverExceptionDuringQuery()
#3 ../vendor/doctrine/dbal/lib/Doctrine/DBAL/Connection.php(1537): Doctrine\DBAL\Connection->handleExceptionDuringQuery()
#4 ../vendor/doctrine/dbal/lib/Doctrine/DBAL/Connection.php(1487): Doctrine\DBAL\Connection->executeStatement()
#5 ../vendor/oxid-esales/oxideshop-ce/source/Core/Database/Adapter/Doctrine/Database.php(799): Doctrine\DBAL\Connection->executeUpdate()
#6 ../vendor/oxid-esales/oxideshop-ce/source/Core/Database/Adapter/Doctrine/Database.php(570): OxidEsales\EshopCommunity\Core\Database\Adapter\Doctrine\Database->executeUpdate()
#7 ../vendor/oxid-esales/oxideshop-ce/source/Application/Model/Shop.php(301): OxidEsales\EshopCommunity\Core\Database\Adapter\Doctrine\Database->execute()
#8 ../vendor/oxid-esales/oxideshop-ce/source/Application/Model/Shop.php(145): OxidEsales\EshopCommunity\Application\Model\Shop->cleanInvalidViews()
#9 ../vendor/oxid-esales/oxideshop-ce/source/Core/DbMetaDataHandler.php(574): OxidEsales\EshopCommunity\Application\Model\Shop->generateViews()
#10 ../vendor/oxid-esales/oxideshop-db-views-generator/src/ViewsGenerator.php(39): OxidEsales\EshopCommunity\Core\DbMetaDataHandler->updateViews()
#11 ../vendor/oxid-esales/oxideshop-db-views-generator/generate_views.php(80): OxidEsales\DatabaseViewsGenerator\ViewsGenerator->generate()
#12 ../vendor/oxid-esales/oxideshop-db-views-generator/oe-eshop-db_views_generate(4): require_once('...')
#13 ../vendor/bin/oe-eshop-db_views_generate(119): include('...')
#14 {main}
Next OxidEsales\Eshop\Core\Exception\DatabaseErrorException: 'myDB.oxv_oxvendor_de' is not VIEW in ../vendor/oxid-esales/oxideshop-ce/source/Core/Database/Adapter/Doctrine/Database.php:959
Stack trace:
#0 ../vendor/oxid-esales/oxideshop-ce/source/Core/Database/Adapter/Doctrine/Database.php(801): OxidEsales\EshopCommunity\Core\Database\Adapter\Doctrine\Database->convertException()
#1 ../vendor/oxid-esales/oxideshop-ce/source/Core/Database/Adapter/Doctrine/Database.php(570): OxidEsales\EshopCommunity\Core\Database\Adapter\Doctrine\Database->executeUpdate()
#2 ../vendor/oxid-esales/oxideshop-ce/source/Application/Model/Shop.php(301): OxidEsales\EshopCommunity\Core\Database\Adapter\Doctrine\Database->execute()
#3 ../vendor/oxid-esales/oxideshop-ce/source/Application/Model/Shop.php(145): OxidEsales\EshopCommunity\Application\Model\Shop->cleanInvalidViews()
#4 ../vendor/oxid-esales/oxideshop-ce/source/Core/DbMetaDataHandler.php(574): OxidEsales\EshopCommunity\Application\Model\Shop->generateViews()
#5 ../vendor/oxid-esales/oxideshop-db-views-generator/src/ViewsGenerator.php(39): OxidEsales\EshopCommunity\Core\DbMetaDataHandler->updateViews()
#6 ../vendor/oxid-esales/oxideshop-db-views-generator/generate_views.php(80): OxidEsales\DatabaseViewsGenerator\ViewsGenerator->generate()
#7 ../vendor/oxid-esales/oxideshop-db-views-generator/oe-eshop-db_views_generate(4): require_once('...')
#8 ../vendor/bin/oe-eshop-db_views_generate(119): include('...')
#9 {main}
thrown in ../vendor/oxid-esales/oxideshop-ce/source/Core/Database/Adapter/Doctrine/Database.php on line 959
corel
February 10, 2025, 12:01pm
7
irgendwie sind es nun weniger Meldung, wenn ich versuche auf 7.0.0 hoch zu laden
user21 $ ./vendor/bin/oe-eshop-db_migrate migrations:migrate
Warning: include(../../vendor/bin/../oxid-esales/oxideshop-doctrine-migration-wrapper/bin/oe-eshop-db_migrate): Failed to open stream: No such file or directory in ../..//vendor/bin/oe-eshop-db_migrate on line 117
Warning: include(): Failed opening '../../vendor/bin/../oxid-esales/oxideshop-doctrine-migration-wrapper/bin/oe-eshop-db_migrate' for inclusion (include_path='.:/usr/share/php') in ../..//vendor/bin/oe-eshop-db_migrate on line 117
user21 $ ./vendor/bin/oe-eshop-db_views_generate
Warning: include(../../vendor/bin/../oxid-esales/oxideshop-db-views-generator/oe-eshop-db_views_generate): Failed to open stream: No such file or directory in ../..//vendor/bin/oe-eshop-db_views_generate on line 117
Warning: include(): Failed opening '../../vendor/bin/../oxid-esales/oxideshop-db-views-generator/oe-eshop-db_views_generate' for inclusion (include_path='.:/usr/share/php') in ../..//vendor/bin/oe-eshop-db_views_generate on line 117
user21 $
corel
February 10, 2025, 12:29pm
8
oder mal anredest herum, eine neue Installation von ^7.2 ist mir ja schon einmal geglückt.
Wie bekomme ich dann meine Daten (db) übertragen?